Intro
| Dificulty | OS | Start Date | End Date | |—|—|—|—| | Very Easy | Linux | 03/06/2022 | 05/06/2022 |
Process
- Common enumeration.
- Use Burp Suite to find new directories.
- Manipulate cookies to be admin and upload files.
- Dirbust the site to find where are the uploads located.
- Upload reverse shell
- Search for other users
- Login with that user and search the user flag.
- Privilege Escalation with SUID.
Burpsuite
- Configure Firefox to send traffic trought the proxy.
- Settings > Search “Proxy” > Settings.
- Change to Manual proxy. Enter Loopback @IP and port 8080
- Disable interception in Burp as it’s
- Proxy > Intercept > Intercept in on (Disable)
Cookies
Found that admin was id=34322 so change the Guest id to simulate he’s the admin. 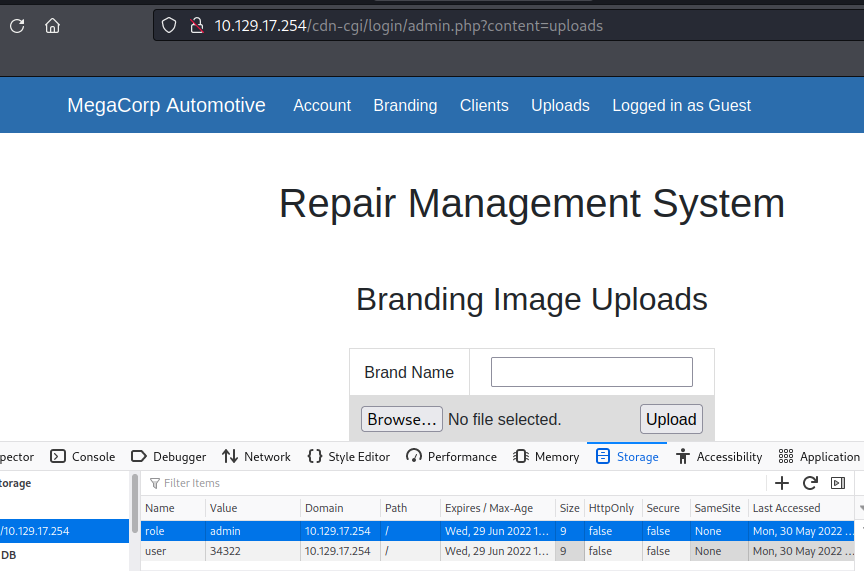
Reverse Shell
Search for common directories. This is a Web Server so is a good idea to check /var/www/html/xxx/. There is a username and a password. Login as robert and search the user.txt.
Find the user group and the files that belong to it. Found executable file in /usr/bin/ named bugtracker that only bugtracker group can execute.